FHACKER CTF WP
Misc
1.ez_jpg
首先会拿到一flag.txt
打开会看见base64的编码的数据:

将其用工具解码:
发现最后的文件末尾好像是jpg的头文件(FF D8 FF E0)所以将字符的顺序进行一个倒置,最后将字符串导入winhex,储存为jpg类型:

发现图片有异常,看看高宽:
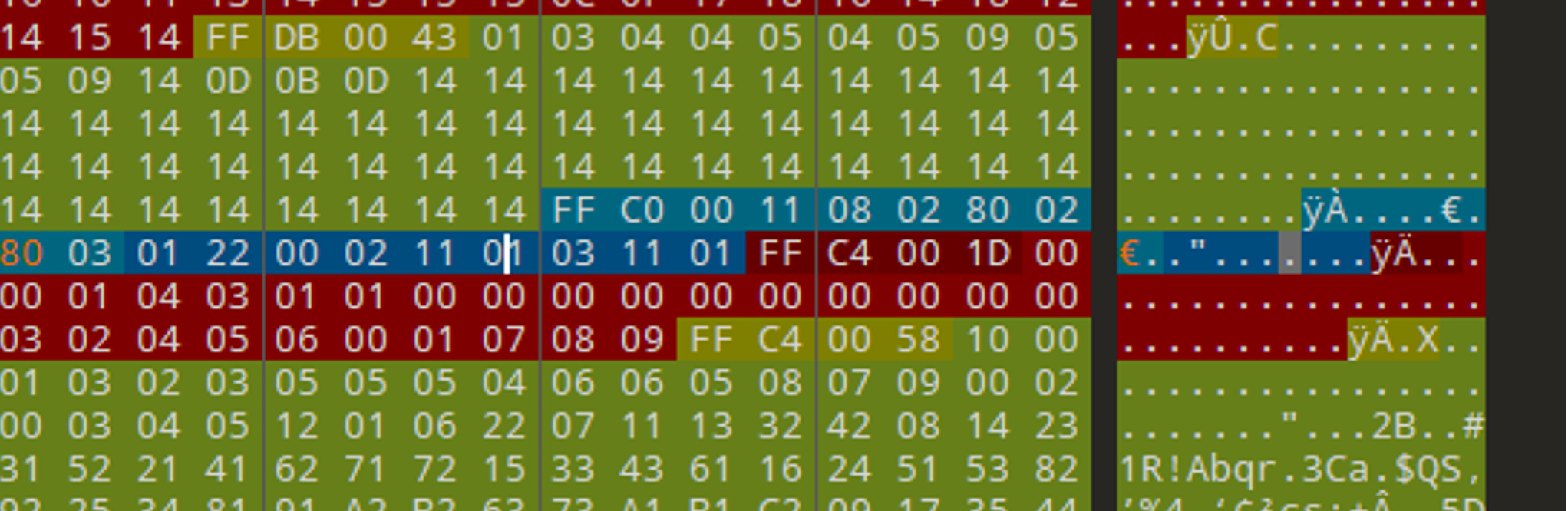
有问题,将宽修改为680也就修改图中标橙色的部分,保存得:

可得flag:SYC{Steg_4nd_Zip_1s_G00d!}
2.舔狗的觉醒
首先下载下来是一个压缩包:
我们用ARCHPR密码爆破从1位到8位:
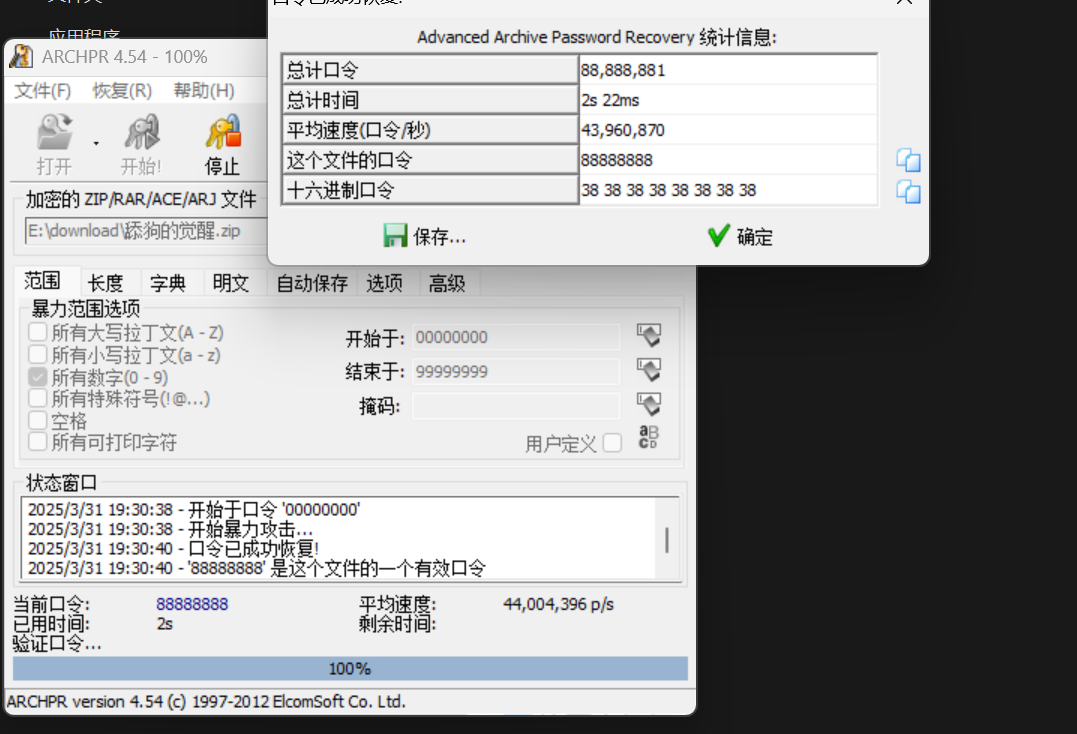
解压可得:
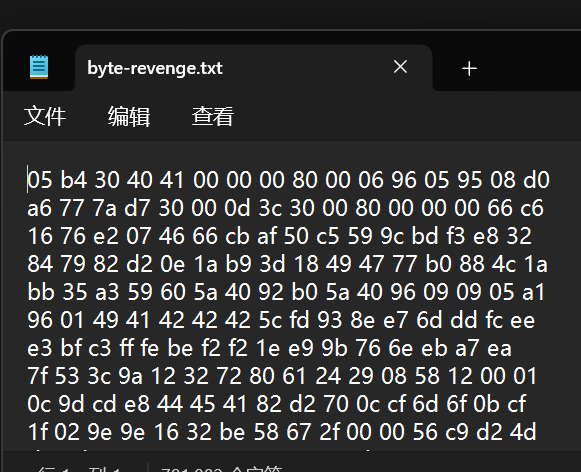
发现有头文件但是被倒置了,可以用程序倒置:
# 读取文件内容
with open('byte-revenge.txt', 'r') as file:
data = file.read().split() # 按空格分割每个字节
# 反转每个字节
swapped_data = [byte[::-1] for byte in data]
# 将处理后的内容写回文件
with open('2.txt', 'w') as file:
file.write(' '.join(swapped_data))转化为文件:
将文件转化为winhex保存为pdf格式得:
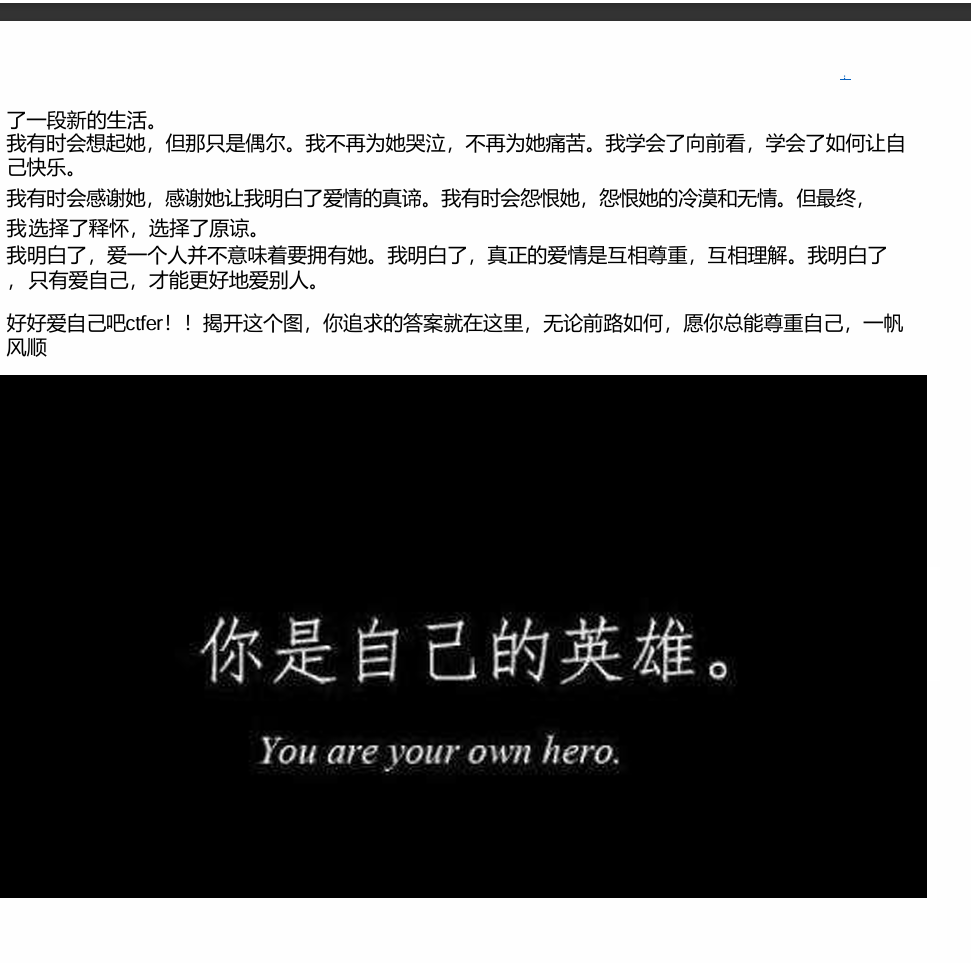
将图片移开得:
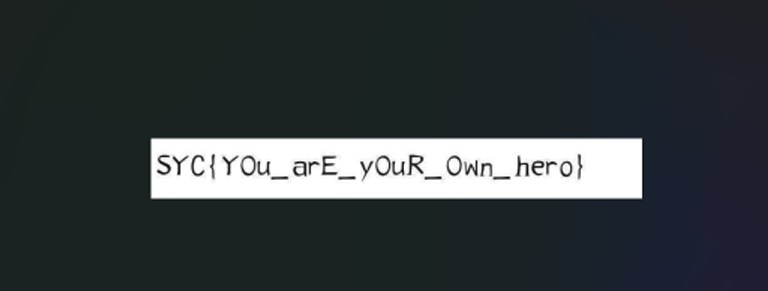
得到Flag:SYC{Y0u_arE_y0uR_0wn_hero}
3.cimbar
附件下载下来得到:
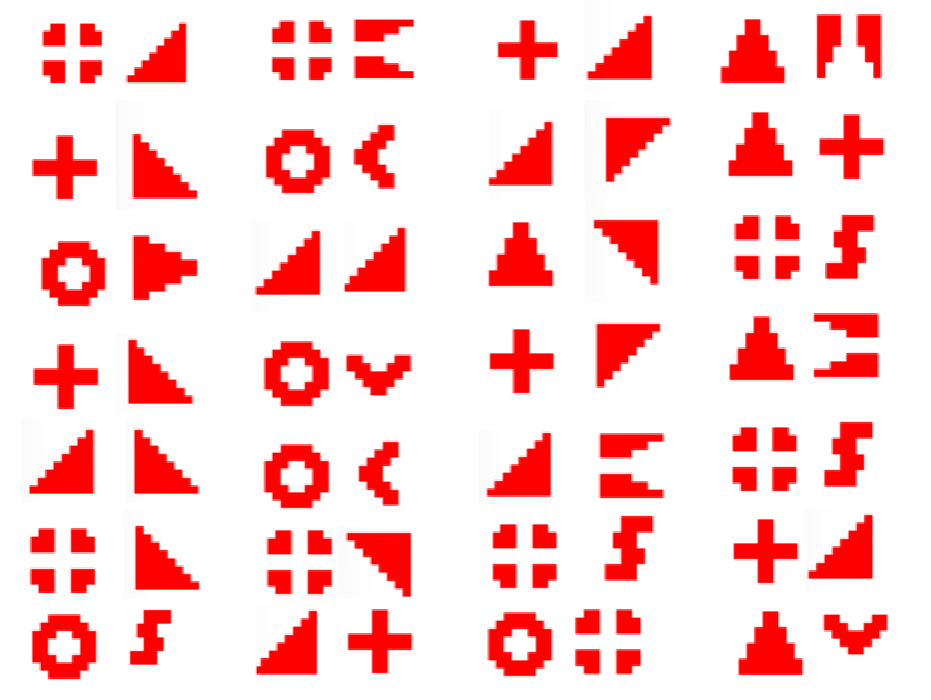
用cimbar密码对照表:

得到二进制数据:
01010011010110010100001101111011010000010110111000110000011101000110100000110011
01110010010111110100000101101101010000000111101000110001011011100011100101011111
0101000101010010010111110100001101101111001101000110010101111101转化为字符串:
SYC{An0th3r_Am@z1n9_QR_Co4e}4.Truth of Word
附件下载下来是一个word文档:
$$
$$
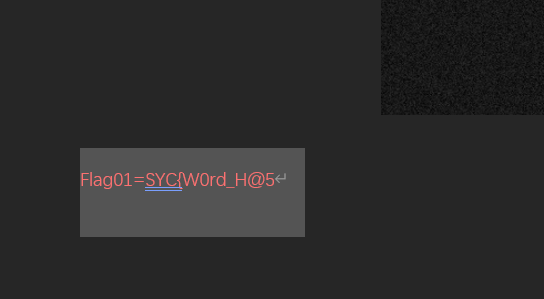
会发现在图片得下方有一个可以被鼠标圈起来的的文字,将其改变颜色可得flag01:
在打开word文档时会提醒有宏,检查运行的宏得到flag02:

由于word文档本质是压缩包,将后缀改为.zip解压可得到一些文件,找到图片所在得文件夹:
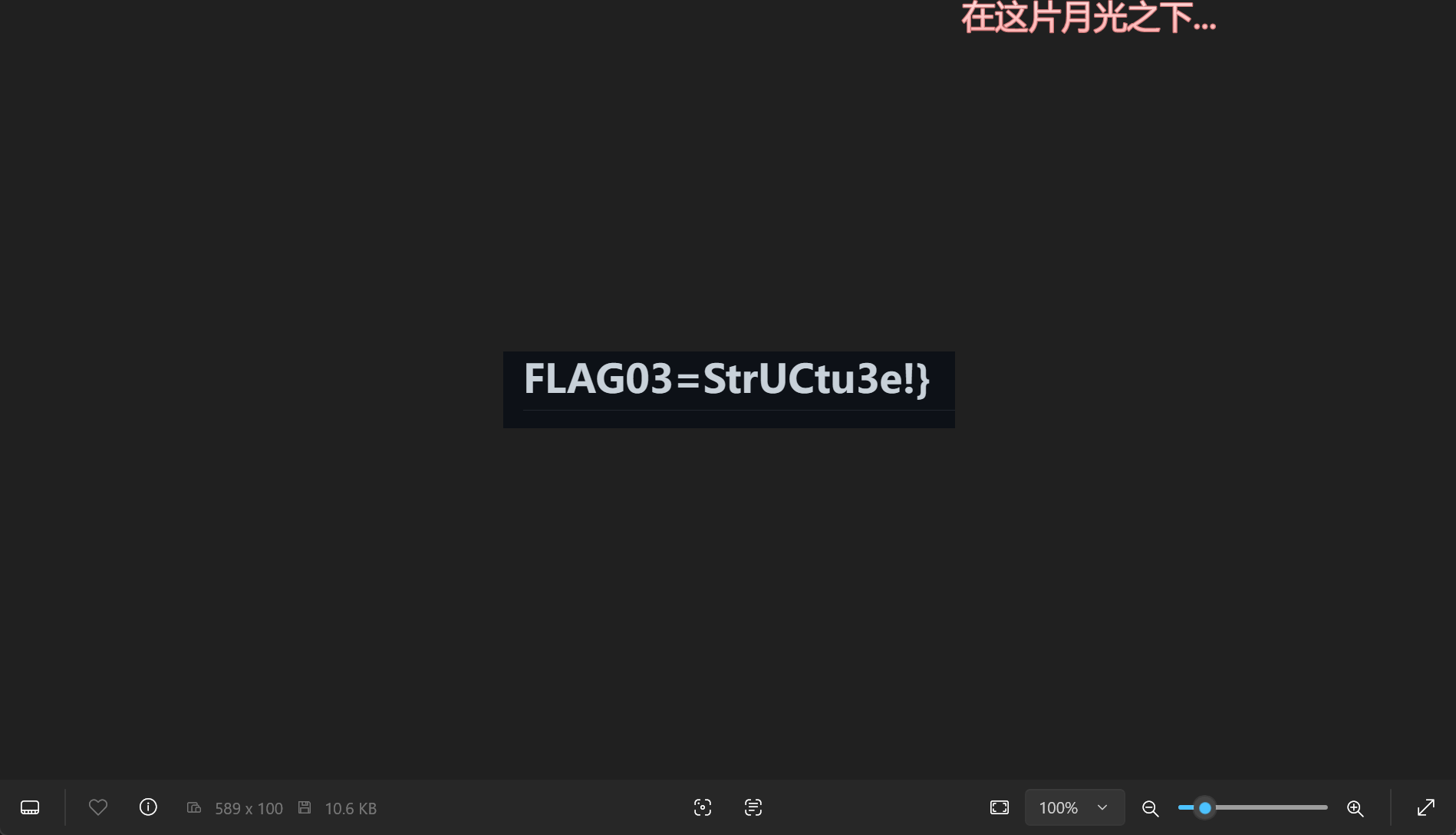
找到flag03
最后得到flag:
SYC{W0rd_H@5@_Ama1n9_StrUCtu3e!}5.乌龟
下载附件,解压发现是一段音频,用RX-SSTV可以得到一个图片:

这判断为音频得密码,把音频丢进Deepsound可得:
用在线logo编码编译运行:
6.雪
附件下载下来发现是一个被加密的压缩包,先用010 Editor打开发现:
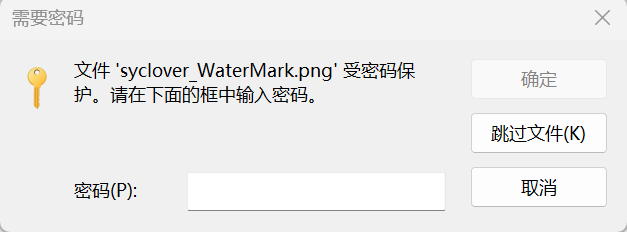
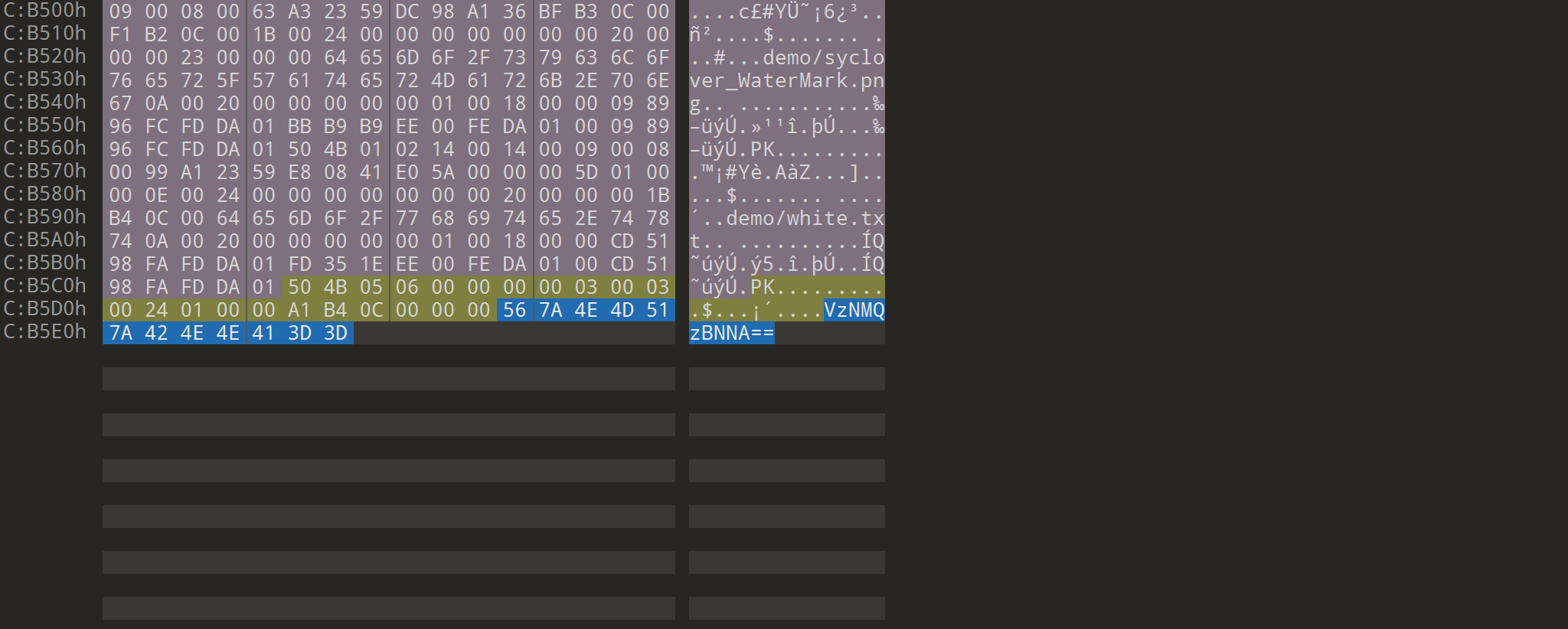
发现数据末尾有一窜字符,发现为base64编码,解码得:W3LC0M4,应该为密码,尝试一下,的确是,发现了文本文件,打开:
还有一张图片,选择用工具处理图片隐写:
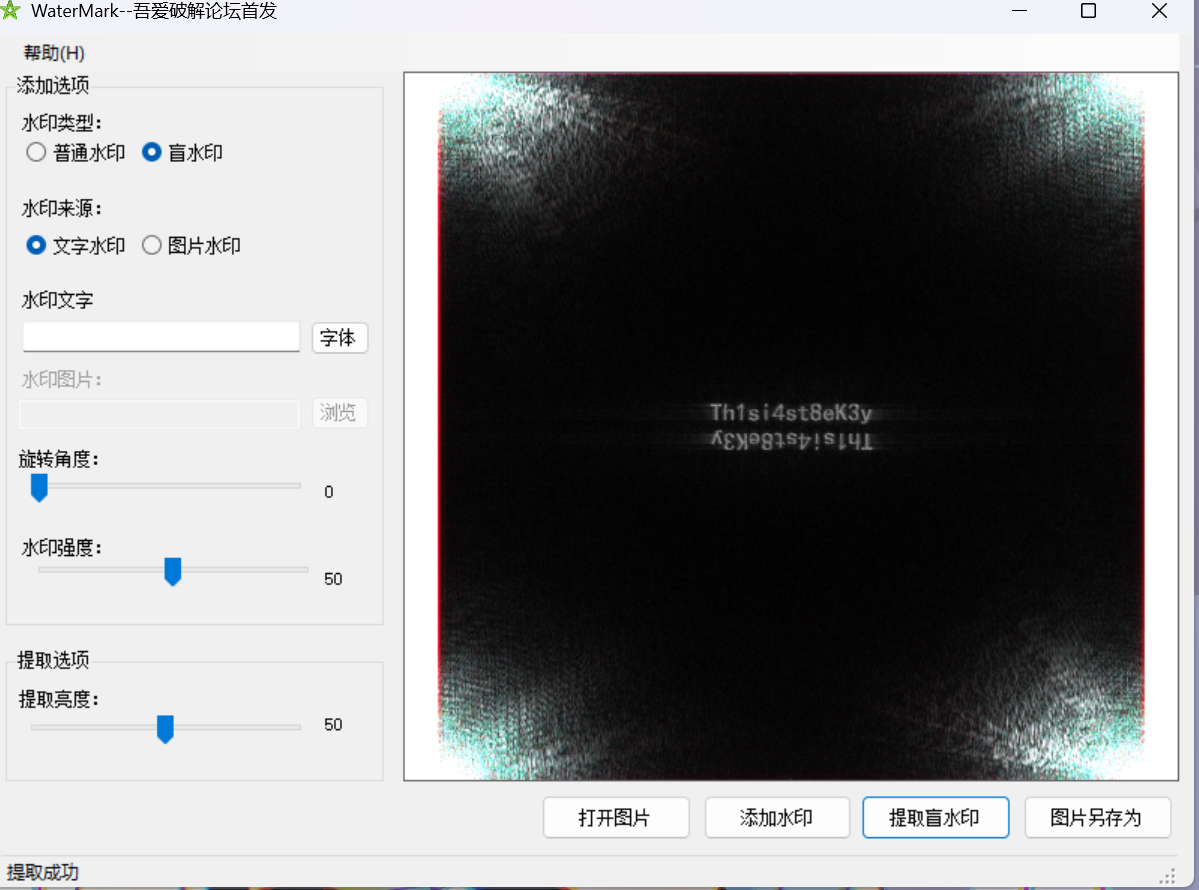
得到snow得密码,用程序解密:
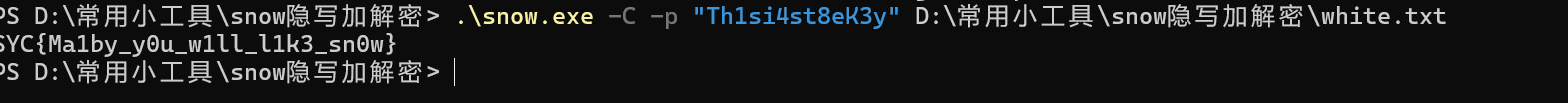
得flag:SYC{Ma1by_y0u_w1ll_l1k3_sn0w}7.ez_pcap_1
直接放一把梭里:
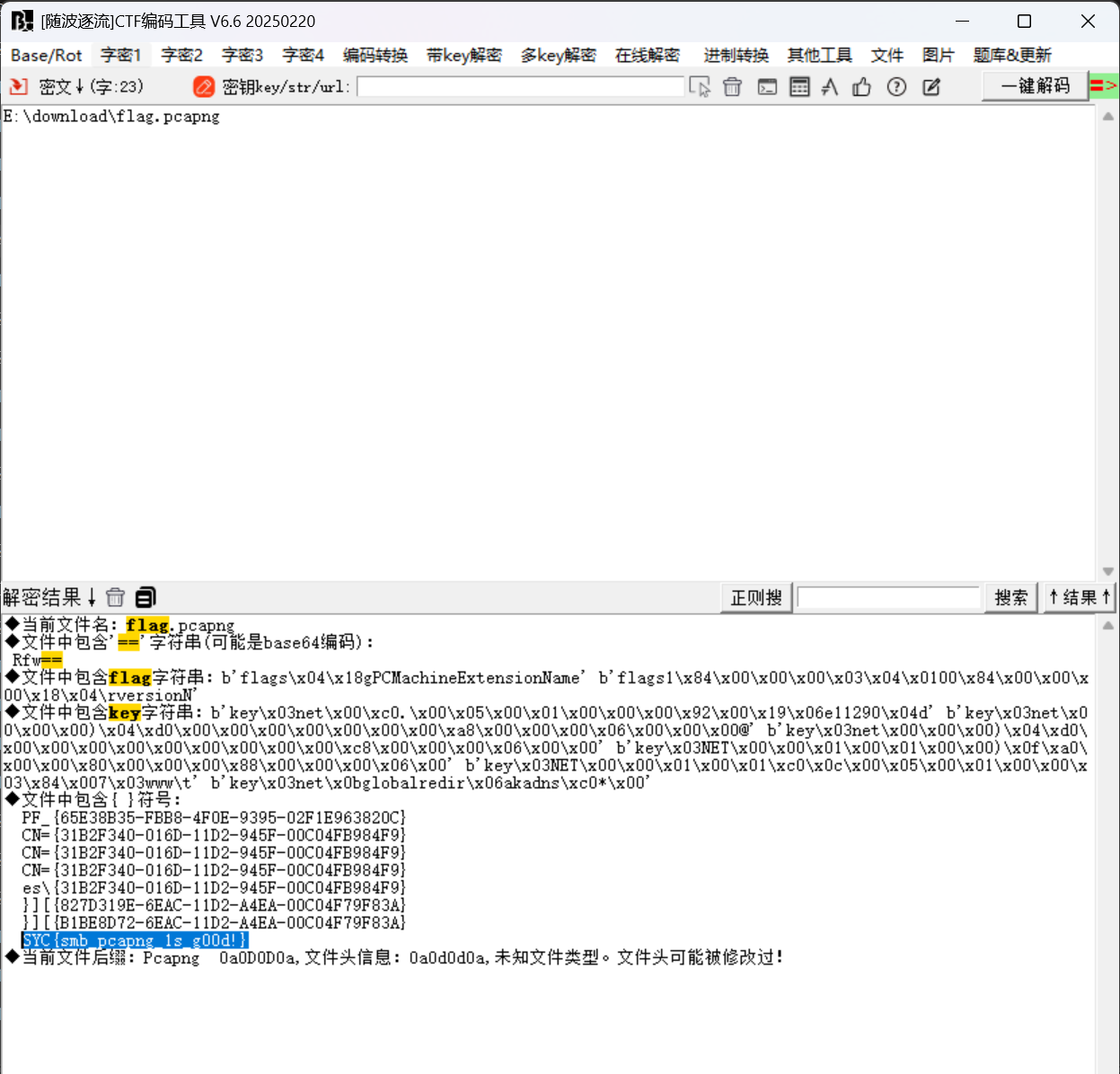
SYC{smb_pcapng_1s_g00d!}8.Secret of Starven
根据分析可得,用SMB导出:
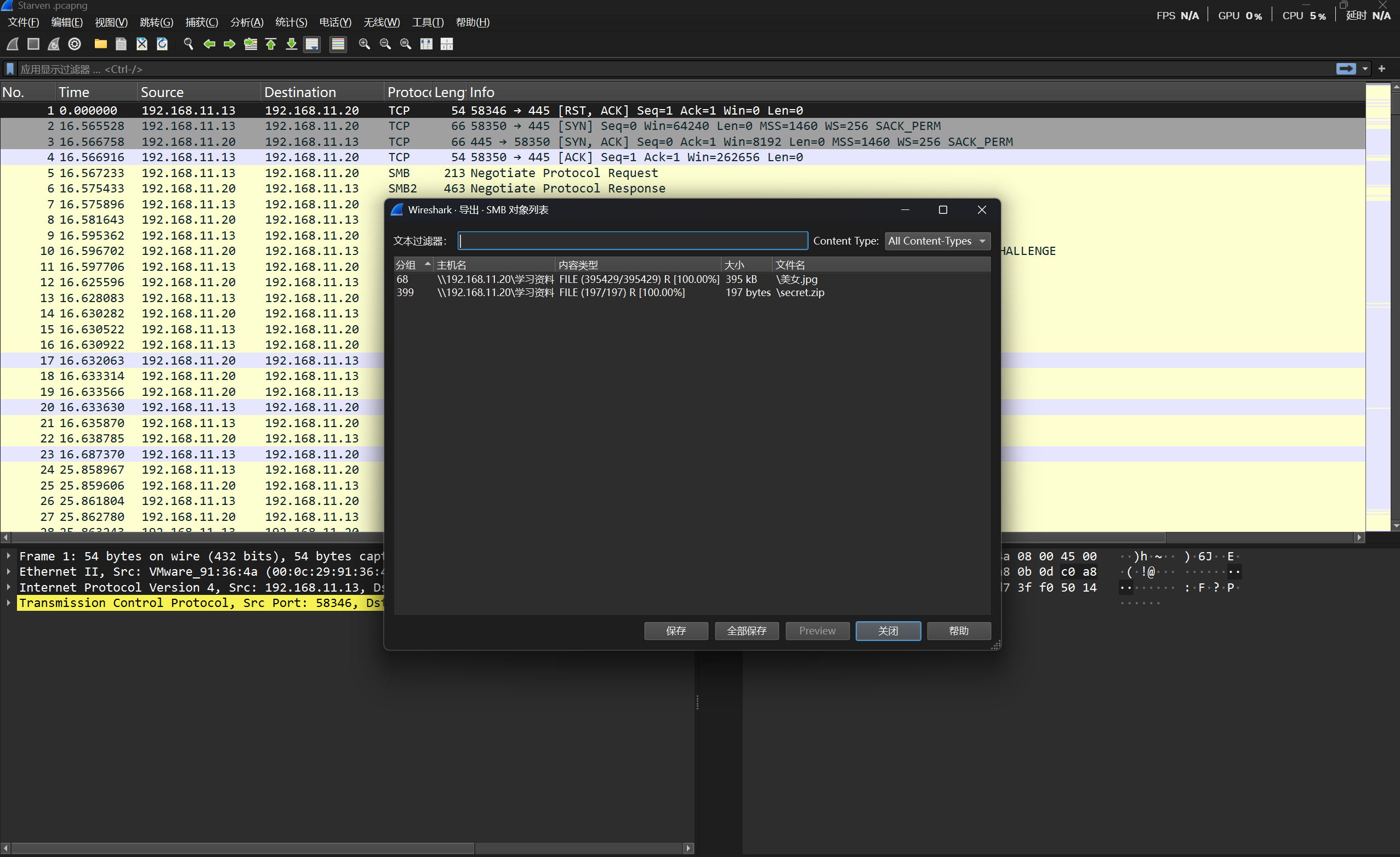
得到一个压缩包和网照,打开压缩包发现被加密了,用010 Editor打开发现文件没有异常,所以尝试密码爆破,得知kali里面有一个数量级较大的字典——rockyou.txt,改为合适得格式后导入字典爆破软件可得:
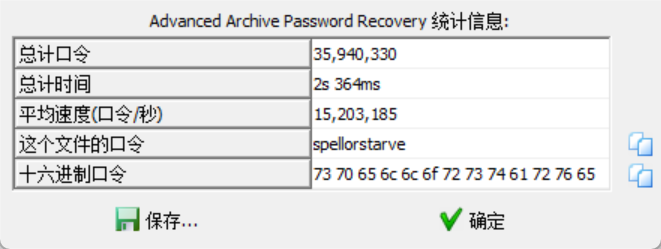
解压得到flag.txt进而得到:
flag:SYC{D0n7_spre0d_St@rven's_s3crEt}WEB
1.100%的⚪

首先打开网址发现需要画一个圆,我们可以直接画,但也可以用更加直接得手段来得到我们想要的,比如直接查看源码搜索,先搜flag,但没那么简单,直接多写几个fff,搜到了:
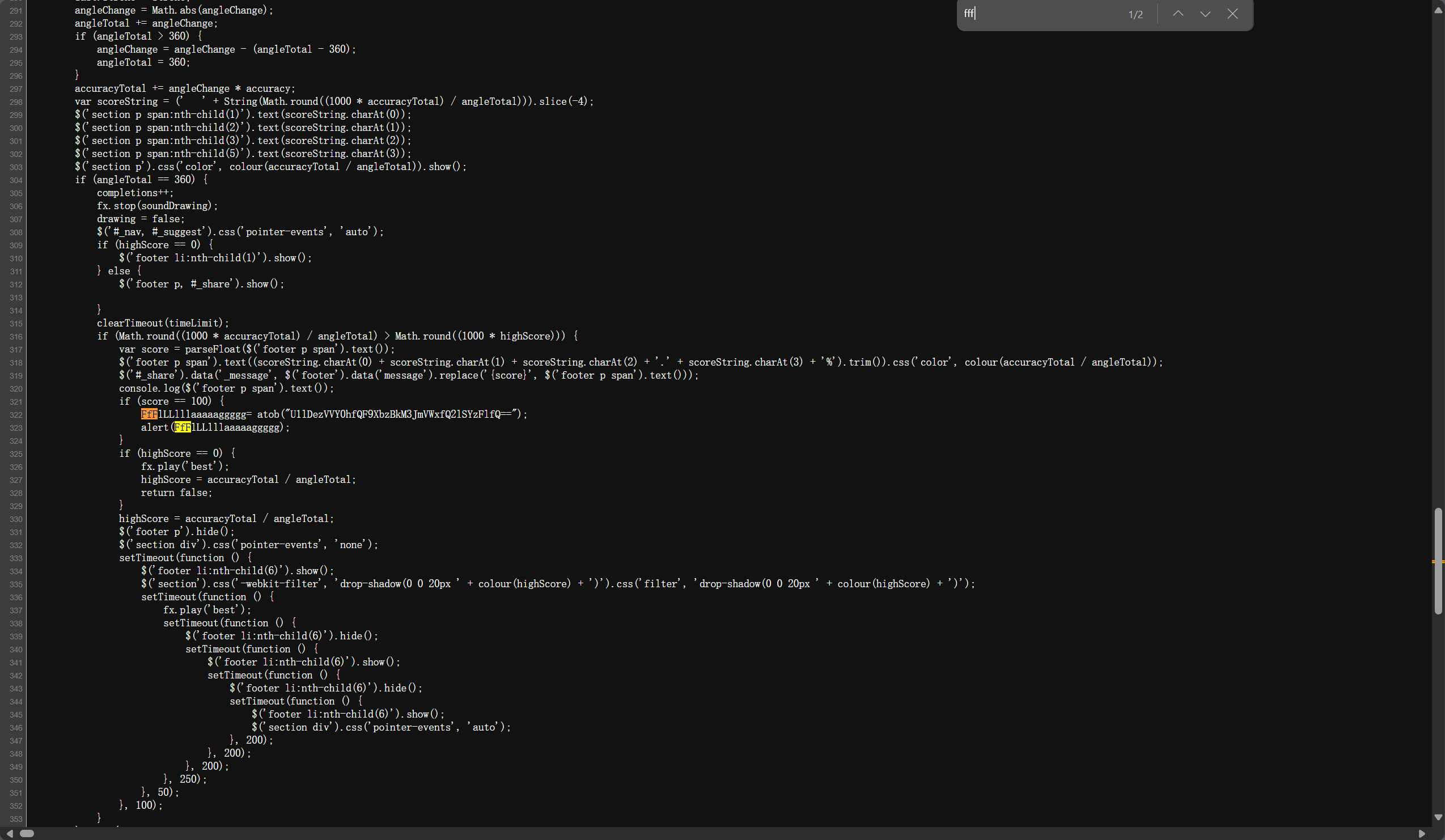
是base64加密,直接解密可以得到flag:
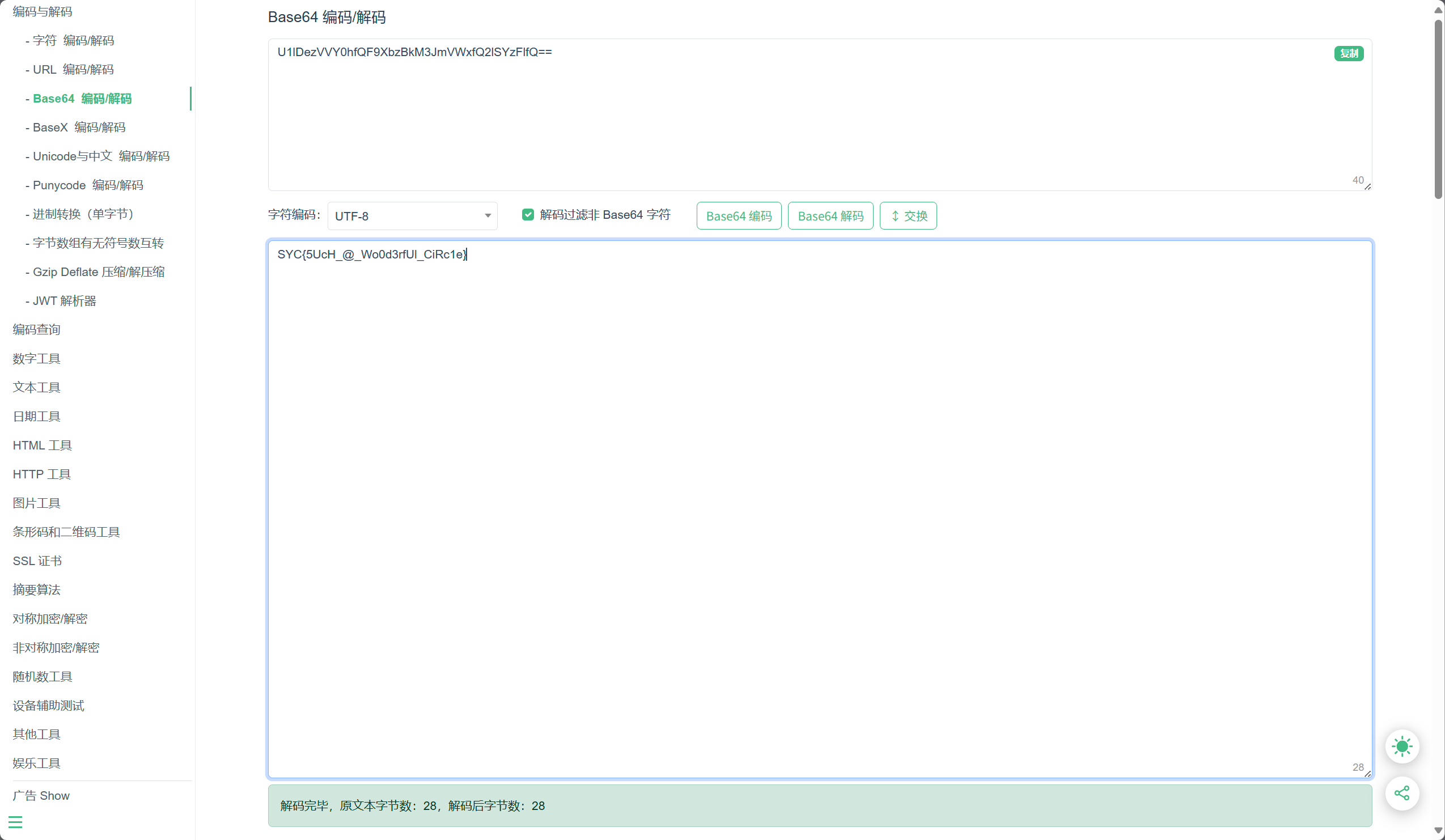
可以得到flag:
SYC{5UcH_@_Wo0d3rfUl_CiRc1e}CRYPTO
1,RSA
基础,直接写解码程序:
from Crypto.Util.number import long_to_bytes
n = 33108009203593648507706487693709965711774665216872550007309537128959455938833
p = 192173332221883349384646293941837353967
q = 172282016556631997385463935089230918399
e = 65537
c = 5366332878961364744687912786162467698377615956518615197391990327680664213847
phi = (p-1)*(q-1)
d = pow(e, -1, phi)
m = pow(c, d, n)
print(long_to_bytes(m).decode())运行程序得到flag:
SYC{RSA_is_easy}2.共模攻击
直接上程序:
from Crypto.Util.number import long_to_bytes
n = 19742875423645690846073637620470497648804310111201409901059297083827103813674034450200432098143959078292346910591785265323563248781526393718834491458926162514713269984791730816121181307827624489725923763353393879316510062227511469438742429290073999388690825732236465647396755899136346150862848924231619666069528077790933176798057396704758072769660663756346237040909579775389576227450505746914753205890194457812893098491264392293949768193694560954874603451253079446652049592976605414438411872223250039782381259212718733455588477129910357095186014496957765297934289263536712574572533650393220492870445376144568199077767
e1, e2 = 911, 967
c1 = 18676091924461946809127036439355116782539894105245796626898495935702348484076501694838877829307466429933623102626122909782775514926293363853121828819237500456062111805212209491398720528499589486241208820804465599279152640624618194425740368495072591471531868392274503936869225072123214869399971636428177516761675388589238329574042518038702529606188240859751459632643230538522947412931990009143731829484941397093509641320264169403755707495153433568106934850283614529793695266717330769019091782929139589939928210818515744604847453929432990185347112319971445630830477574679898503825626294542336195240055995445217249602983
c2 = 4229417863231092939788858229435938841085459330992709019823280977891432565586698228613770964563920779991584732527715378842621171338649745186081520176123907689669636473919678398014317024138622949923292787095400632018991311254591786179660603414693984024161009444842277220189315861986306573182865656366278782315864366857374874763243428496061153290565891942968876789905670073321426112497113145141539289020571684634406829272902118484670099097148727072718299512735637087933649345419433312872607209633402427461708181971718804026293074540519907755129917132236240606834816534369171888633588190859475764799895410284484045429152
# 计算贝祖系数
def extended_gcd(a, b):
if b == 0:
return a, 1, 0
else:
g, x, y = extended_gcd(b, a % b)
return g, y, x - (a // b) * y
gcd, a, b = extended_gcd(e1, e2)
# 处理负数指数
if a < 0:
c1_inv = pow(c1, -1, n)
part1 = pow(c1_inv, -a, n)
else:
part1 = pow(c1, a, n)
if b < 0:
c2_inv = pow(c2, -1, n)
part2 = pow(c2_inv, -b, n)
else:
part2 = pow(c2, b, n)
m = (part1 * part2) % n
print(long_to_bytes(m).decode())运行就可以得到答案flag:
SYC{U_can_really_attack}3.XOR
直接上代码:
from Crypto.Util.number import long_to_bytes
from pwn import xor
# 题目给定数据
e2 = 10706859949950921239354880312196039515724907
f1 = 4585958212176920650644941909171976689111990
f2 = 3062959364761961602614252587049328627114908
# 逆向计算原始加密数据
enc = e2 ^ f1 ^ f2
enc_bytes = long_to_bytes(enc)
# 尝试不同前导零补齐方式
found = False
for pad in range(0, 5):
padded = b'\x00' * pad + enc_bytes
# 检查长度是否足够提取密钥
if len(padded) < 4:
continue
# 通过已知flag头恢复密钥
try:
key = xor(padded[:4], b'SYC{')
except:
continue
# 循环异或解密完整内容
try:
flag = xor(padded, key)
if flag.startswith(b'SYC{'):
print(f"[+] Flag found with {pad} padding: {flag.decode()}")
found = True
break
except:
continue
if not found:
print("[-] Failed to recover flag with tested padding")运行可得flag:
SYC{a_part_0f_X0R}4.ncoCRT
没什么好说的直接上代码:
from Crypto.Util.number import long_to_bytes
def extended_gcd(a, b):
if b == 0:
return (a, 1, 0)
else:
g, x, y = extended_gcd(b, a % b)
return (g, y, x - (a // b) * y)
def crt_merge(a1, m1, a2, m2):
g, x, y = extended_gcd(m1, m2)
if (a2 - a1) % g != 0:
return None
lcm = m1 // g * m2
tmp = (a1 + (x * (a2 - a1) // g) % (m2 // g) * m1) % lcm
return (tmp, lcm)
p = [
1921232050179818686537976490035,
2050175089402111328155892746480,
1960810970476421389691930930824,
1797713136323968089432024221276,
2326915607951286191807212748022
]
c = [
1259284928311091851012441581576,
1501691203352712190922548476321,
1660842626322200346728249202857,
657314037433265072289232145909,
2056630082529583499248887436721
]
current_a, current_m = c[0], p[0]
for i in range(1, 5):
result = crt_merge(current_a, current_m, c[i], p[i])
if not result:
print(f"Failed to merge equation {i}")
exit()
current_a, current_m = result
# 转换为字节并去除填充
m_bytes = long_to_bytes(current_a).rstrip(b'\x01')
print("Flag:", m_bytes.decode())运行程序即可得到flag:
SYC{wha+s_wr0n9!_CRT_bu+_n0+_<0mpr1me!}5.凯撒加密
先拿到加密的文本:
YEI{CKRIUSK_ZU_2024_MKKQ_INGRRKTMK}已知凯撒加密的是具有偏移量的,我们用SYC来确定偏移量,偏移量为20;
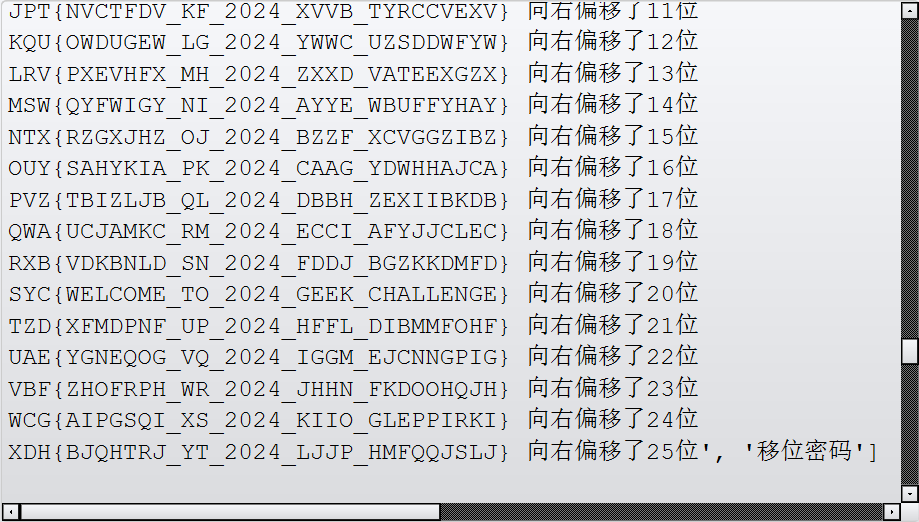
得到flag:
SYC{WELCOME_TO_2024_GEEK_CHALLENGE}- 6.ezRSA 直接上代码,需要在sagemath上跑: ```python from sage.all import * # 校验值 n = 98776098002891477120992675696155328927086322526307976337988006606436135336004472363084175941067711391936982491358233723506086793155908108571814951698009309071244571404116817767749308434991695075517682979438837852005396491907180020541510210086588426719828012276157990720969176680296088209573781988504138607511 c = 9379399412697943604731810117788765980709097637865795846842608472521416662350816995261599566999896411508374352899659705171307916591351157861393506101348972544843696221631571188094524310759046142743046919075577350821523746192424192386688583922197969461446371843309934880019670502610876840610213491163201385965 h = 111518648179416351438603824560360041496706848494616308866057817087295675324528913254309319829895222661760009533326673551072163865 bits = 150 # 计算 h_plus 和 M h_plus = h + 2023 M = h_plus // 2024 # 定义多项式环 P = PolynomialRing(Zmod(n), 'x') x = P.gen() # 构造多项式 (M + x)^3 - c f = (M + x)^3 - c # 尝试小根 try: x0 = f.small_roots(X=2^bits, beta=0.5) if x0: x = x0[0] m = M + x # 验证解 if (M + x)^3 == c: # 转换为字节 hex_str = hex(m)[2:] if len(hex_str) % 2 != 0: hex_str = '0' + hex_str flag = bytes.fromhex(hex_str) print("Flag:", flag.decode()) else: print("Solution is invalid") else: print("No solution found") except Exception as e: print("Error:", e)
跑出:
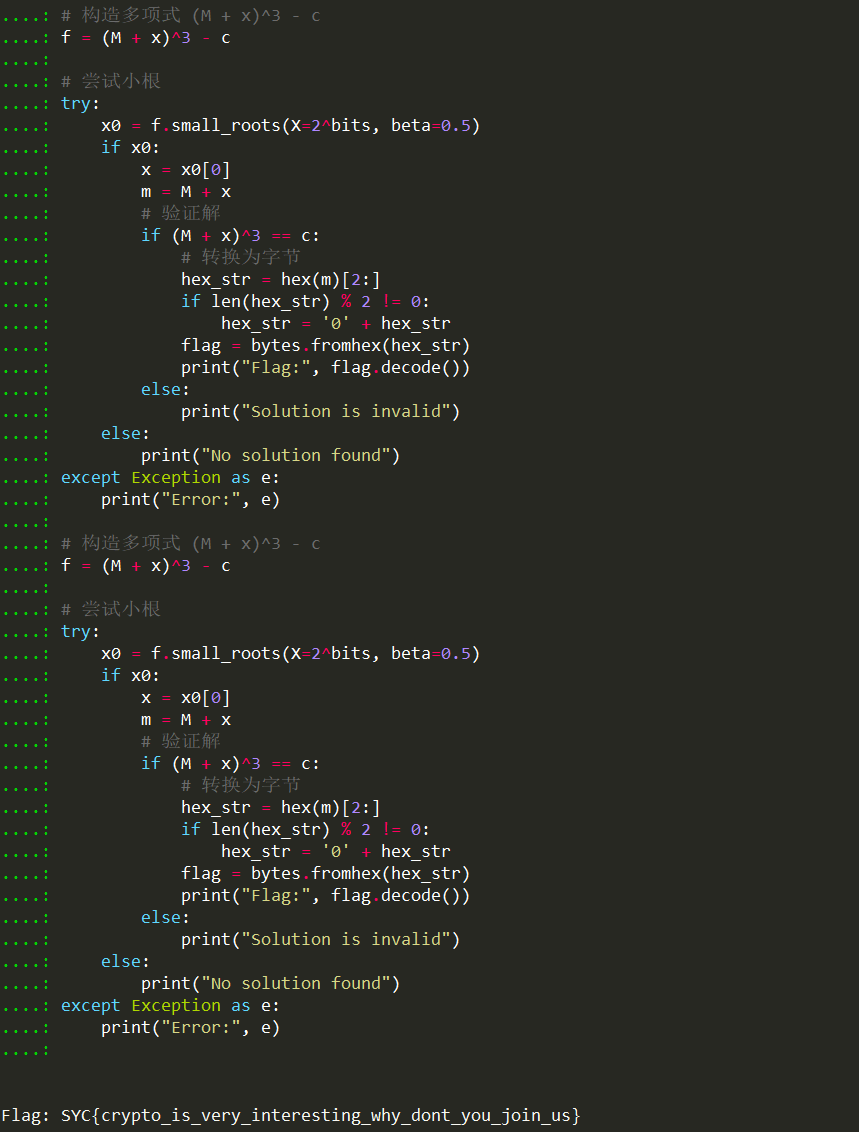
可以得到flag:
SYC{crypto_is_very_interesting_why_dont_you_join_us}7.dp
直接上代码:
from Crypto.Util.number import inverse, long_to_bytes
import math
c = 127916287434936224964530288403657504450134210781148845328357237956681373722556447001247137686758965891751380034827824922625307521221598031789165449134994998397717982461775225812413476283147124013667777578827293691666320739053915493782515447112364470583788127477537555786778672970196314874316507098162498135060
n = 157667866005866043809675592336288962106125998780791920007920833145068421861029354497045918471672956655205541928071253023208751202980457919399456984628429198438149779785543371372206661553180051432786094530268099696823142821724314197245158942206348670703497441629288741715352106143317909146546420870645633338871
e = 65537
dp = 2509050304161548479367108202753097217949816106531036020623500808413533337006939302155166063392071003278307018323129989037561756887882853296553118973548769
# 选择a=2计算可能的p
a = 2
exponent = e * dp
m = pow(a, exponent, n)
p = math.gcd(m - a, n)
if p > 1 and n % p == 0:
q = n // p
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
m = pow(c, d, n)
print("Flag:", long_to_bytes(m).decode())
else:
# 如果a=2不成功,尝试其他a值
found = False
for a in range(3, 10):
m = pow(a, e * dp, n)
p = math.gcd(m - a, n)
if p > 1 and n % p == 0:
q = n // p
phi = (p - 1) * (q - 1)
d = inverse(e, phi)
m = pow(c, d, n)
print("Flag:", long_to_bytes(m).decode())
found = True
break
if not found:
print("Failed to find p with a=2 to 9. Try another method.")运行就得flag:
SYC{welcome_to_crypto}
have_fun_- 接下是重头戏: # 史上最没节操的游戏: 首先为一个小型galgame,只是不过很是难蚌。  首先非常的容易,我们先打一个逆转裁判:  在这里我们的名字会被更改,但不用慌,维吉尼亚来拯救你: 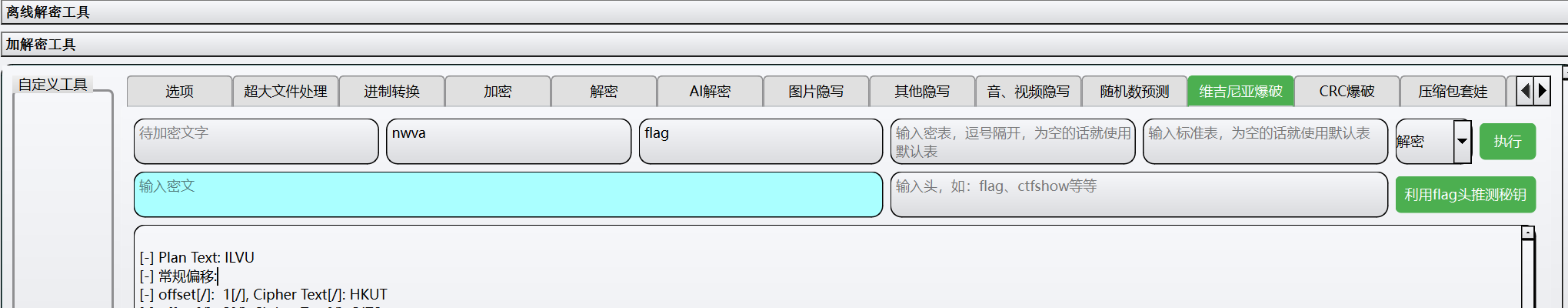 这样就得到了我们想要的flag4:
好接下在前往游乐场:
做些流量分析题就行了:
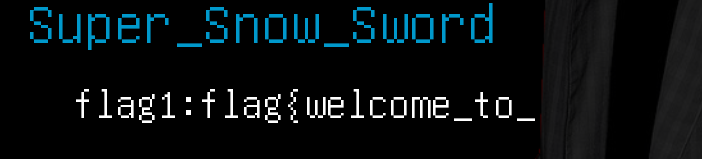
就得到flag2:
flag{welcome_to_
现在该去电影院了,去见贝利亚,是音频隐写,去除杂音,用sstv听一下:
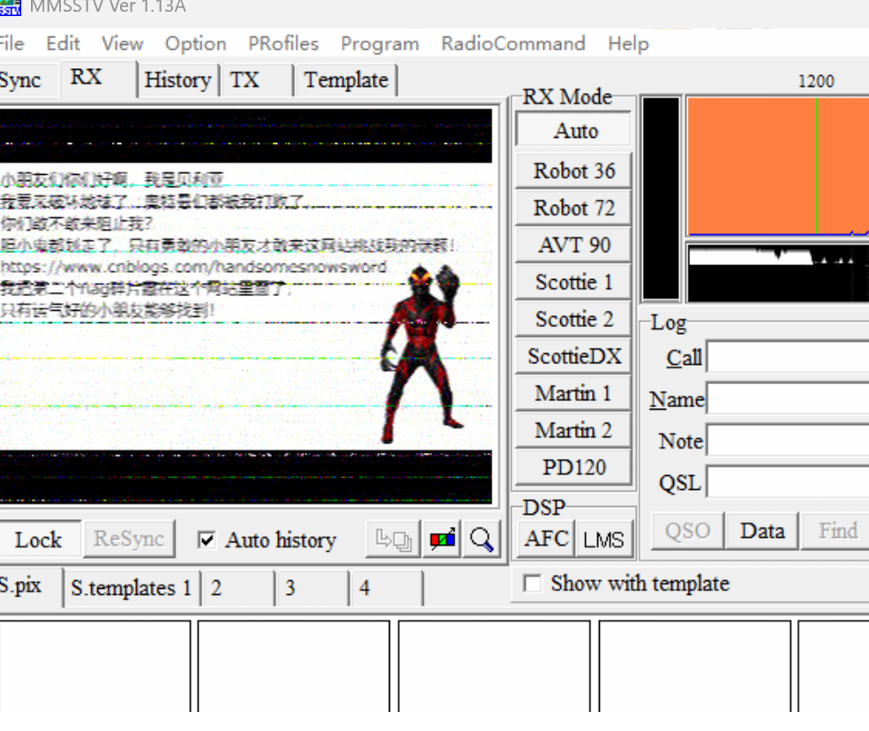
得到网址:
https://www.cnblogs.com/handsomesnowsword
能访问到出题人的博客:
界面多刷新几次,我刷了两次就出来了:

得到flag2:
RehPY_
现在我们走到了漫展,见到的无头学姐,需要我们来帮她来找头,是电子取证:
找到网址:
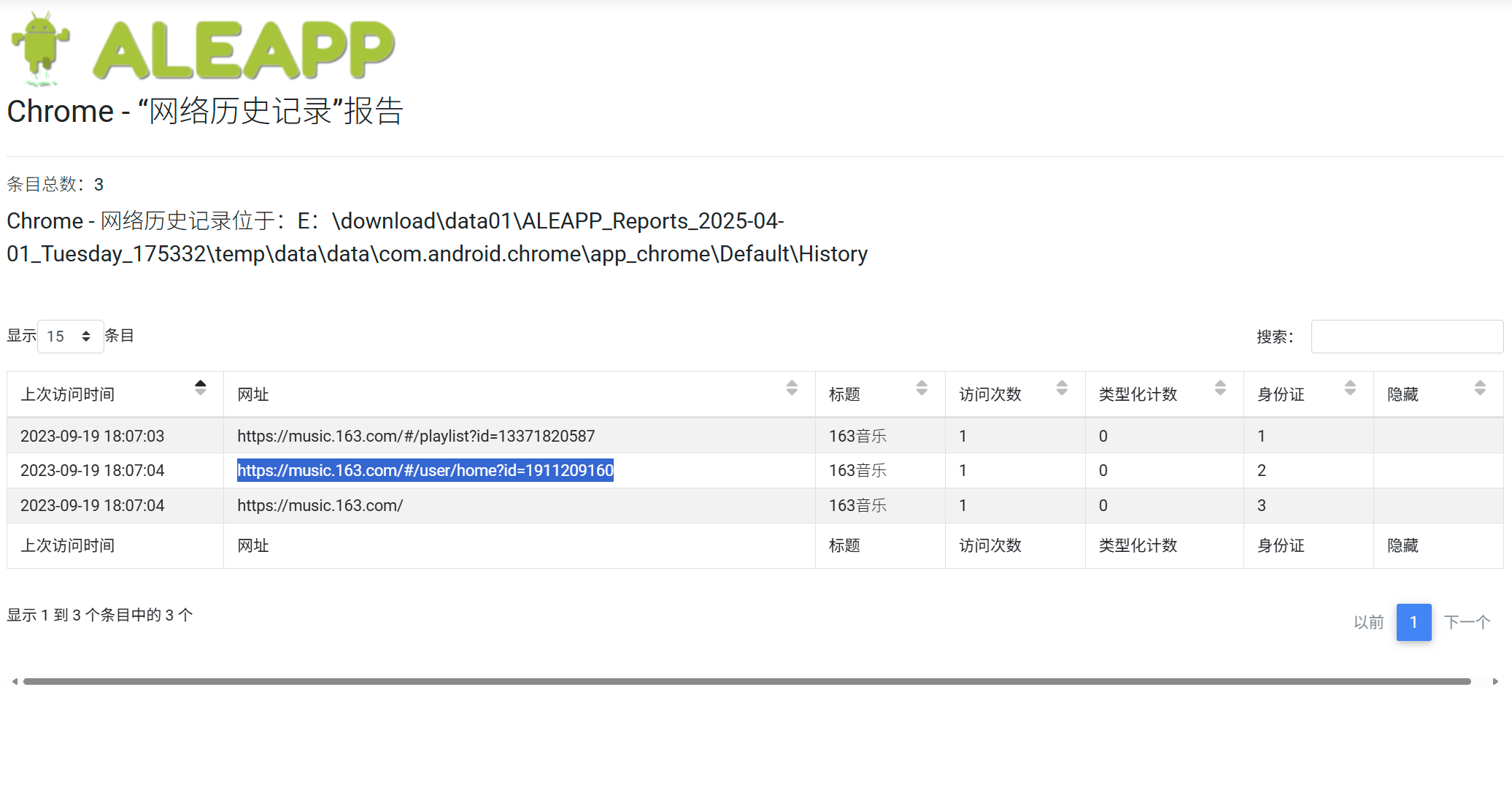
找到藏头诗:
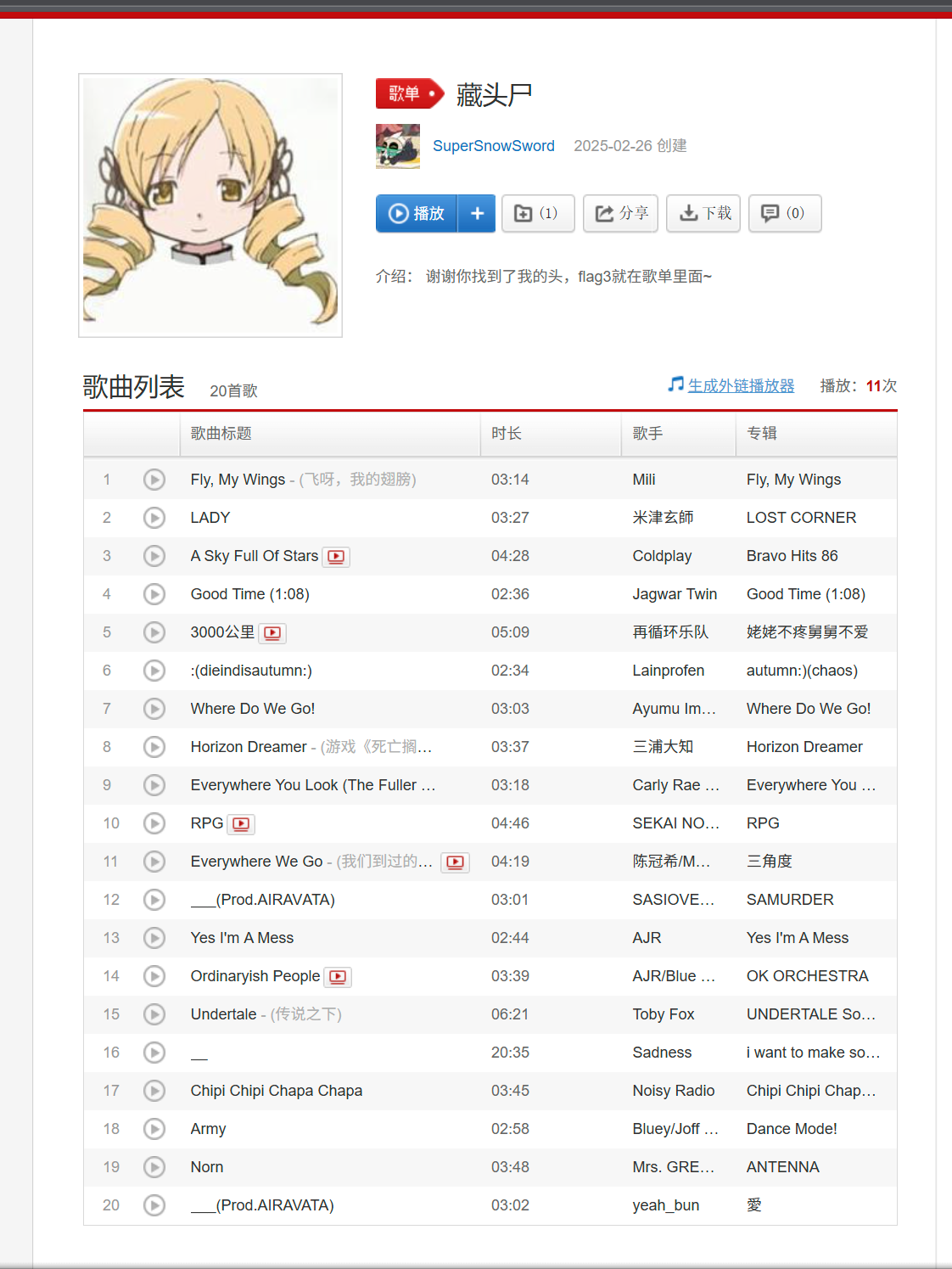
得到flag3:
WHERE_YOU_CAN_
现在终于到了最终的步骤:
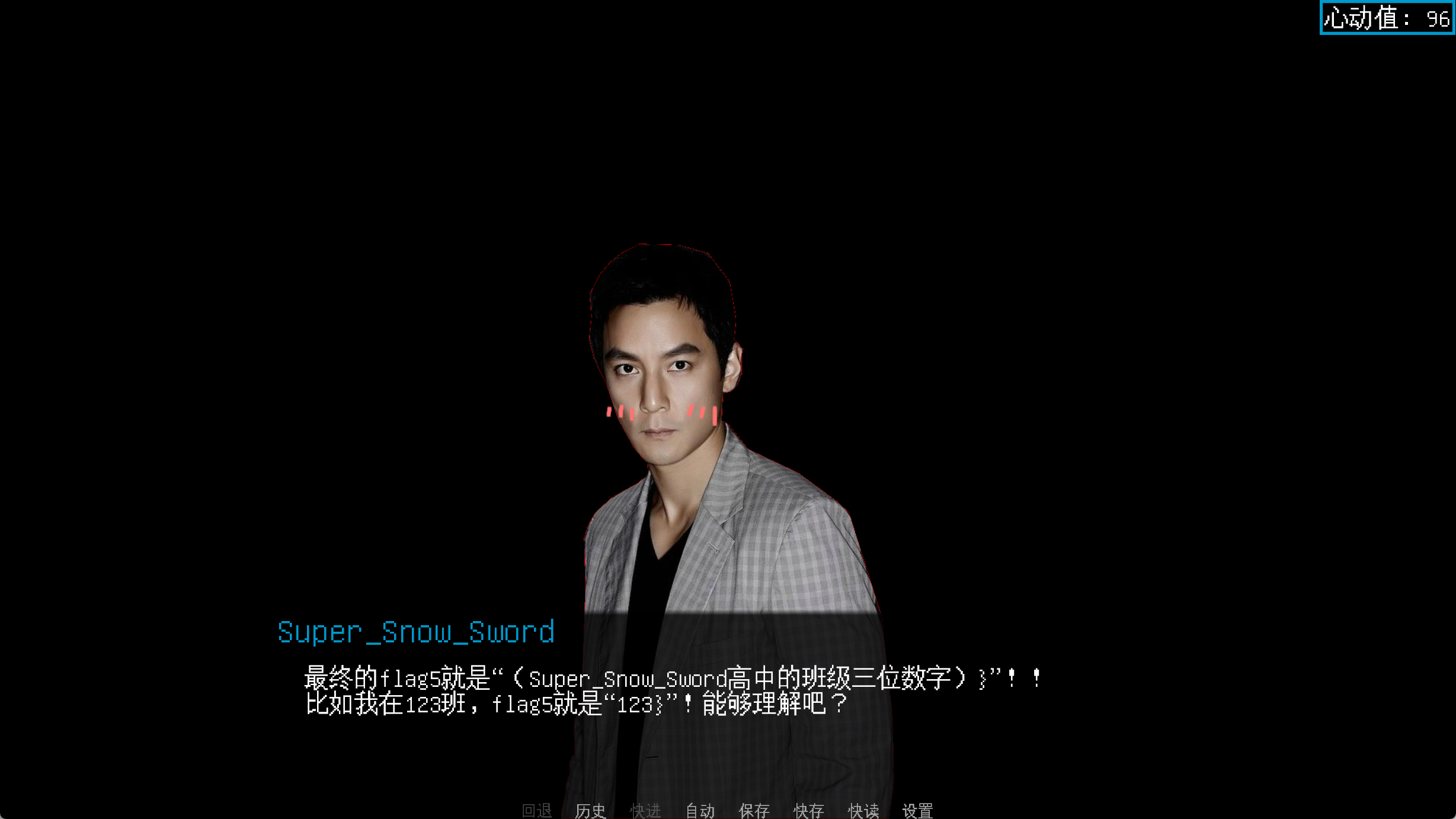
使用社会工程学得到:

班级为324,也就是flag5:
324
最后拼得flag:
flag{welcome_to_RehPY_WHERE_YOU_CAN_have_fun_324}
2.友谊地久天长
发现是一个邮箱文件,很明显,我们使用任意的邮箱进行打开,会得到一张损坏的图片和友谊地久天长的音频
在邮件中有提醒,不要再音频中太过倾注自己的感情:
直接对图片进行检测:
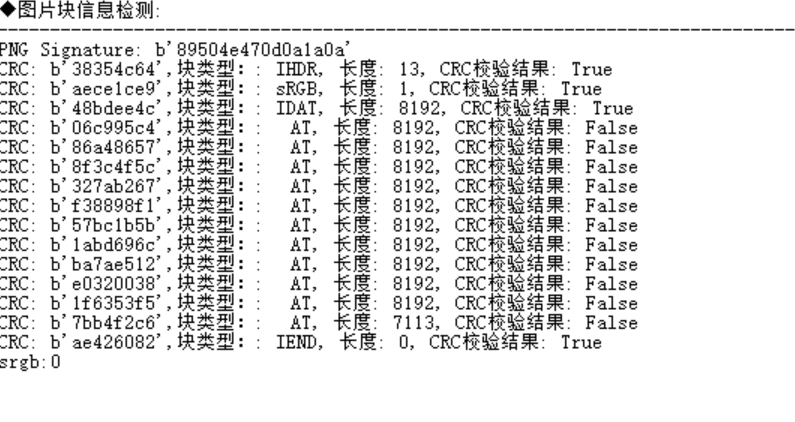
进行修复可得,(注意!要进行分段修复):

用二维码检测得到密钥:
Super_Snow_Sword_is_so_handsome
音频解密得到真得音频,然后直接formost直接提取文件得到:

然后对图片用Stegsolve得到:

然后对图片用:
最后翻页可得:
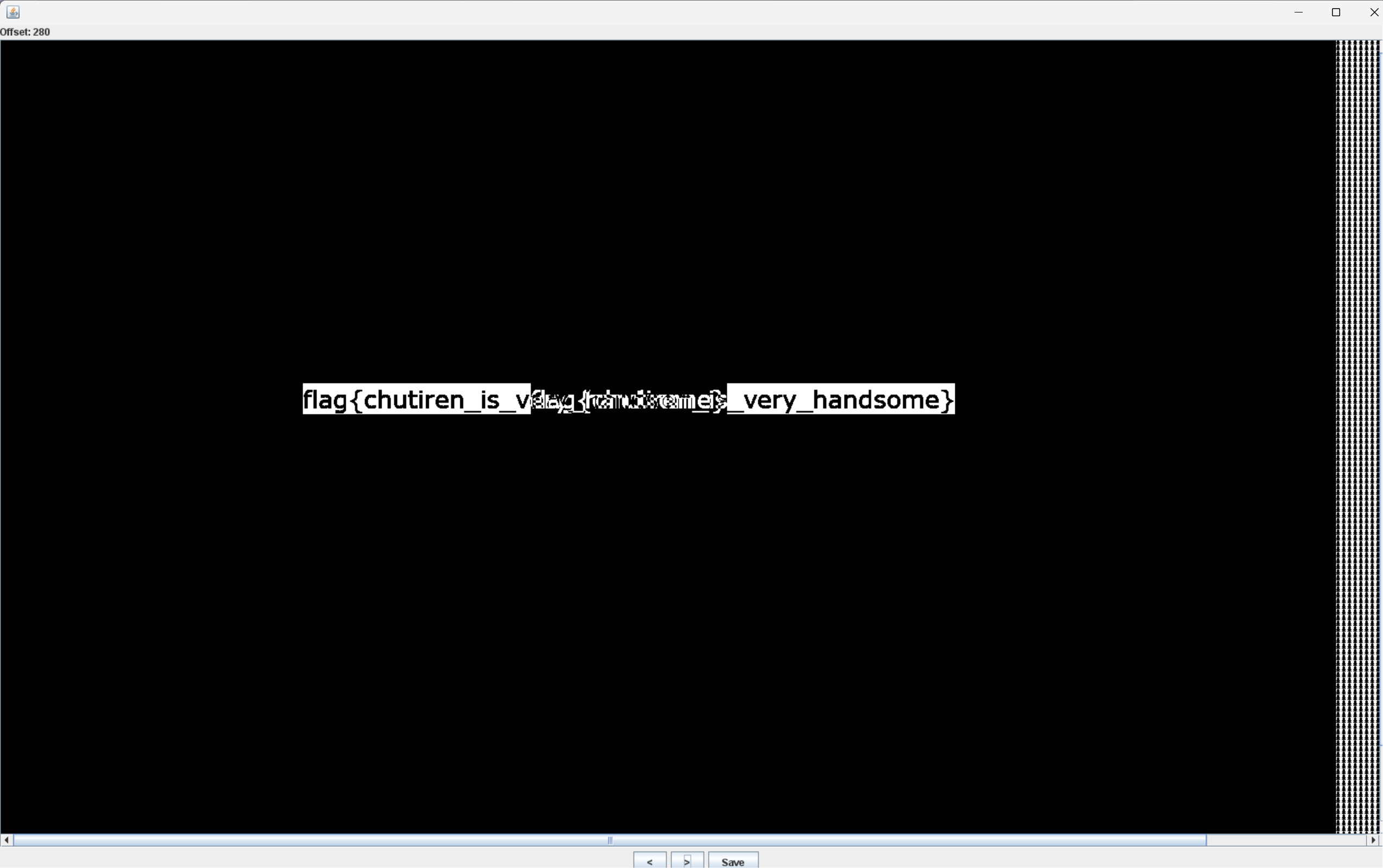
可得flag:
flag{chutiren_is_very_handsome}
